SSH Keys with Git
Using username-passwords for Git authentication used to be common, but from a security standpoint, it’s far from ideal as they are easy to hack if targeted, inconvenient among developers as you need to authenticate every time & deprecated by Git hosting platforms
Instead, platforms transitioned to SSH Keys and Personal Access Tokens (PATs) for secure authentication.
Why SSH Keys?
SSH keys provide stronger security, eliminate the need to repeatedly enter credentials, and are widely used among developers and organizations.
How Do SSH Keys Provide Stronger Security?
SSH keys use asymmetric encryption algorithms, such as Ed25519, RSA and other algorithms to establish secure authentication. Unlike passwords, which can be easily compromised through brute force attacks or phishing, SSH keys are significantly harder to crack due to their cryptographic strength:
- Ed25519: Uses the Edwards-curve Digital Signature Algorithm (EdDSA) for enhanced security, optimized for speed and smaller key sizes.
- RSA (2048-bit or higher): A widely used public-key encryption system, though it requires larger key sizes (e.g., 3072-bit or 4096-bit) to maintain security.
By leveraging these cryptographic algorithms, SSH authentication ensures secure communication between the client and server, preventing unauthorized access.
Cryptography is the practice of securing information by converting it into an unreadable format using mathematical algorithms, ensuring confidentiality, integrity, and authentication.
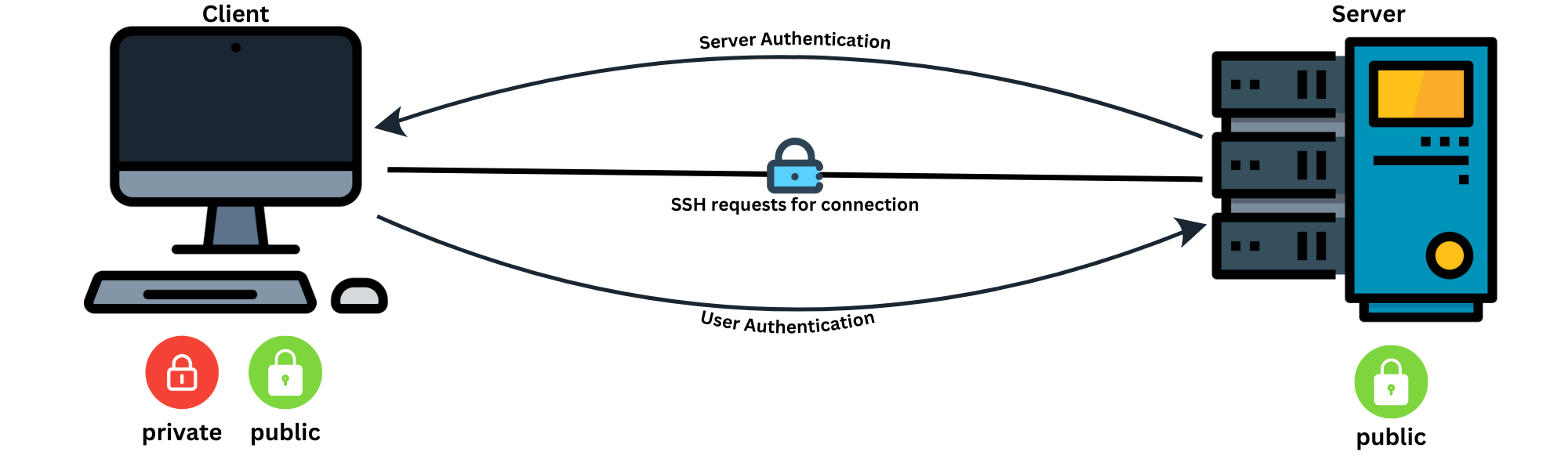
SSH keys work in pairs:
- Private Key (
id_ed25519) → Keep it secret! Never share it. - Public Key (
id_ed25519.pub) → Safe to share, uploaded to the Git server.
If someone gets your private key, they have full access to your GitHub account
- The private key remains on your system.
- The public key is uploaded to the Git server.
Behind the scenes
When you push or pull from your Git repository using SSH, this is what happens behind
- Your computer(client) uses SSH to request authentication to the remote server
- The remote server(Git) now checks if it has your corresponding public key
- If the public key is found, the server generates a random challenge, encrypts it with the public key, and sends it back
- Now, your computer(client) tries to decrypt the puzzle using the private key and sends the proof back
- If the decryption is successful, you gain access to the server to do your changes
💡 Only your private key can decrypt the puzzle of public key
Why Use Ed25519 Instead of RSA?
Modern SSH implementations recommend Ed25519 over RSA because they are more secure, fast & smaller key size (256-bit Ed25519 ≈ 3000-bit RSA)
Setting Up SSH for GitHub
1. Generate SSH key (if not already done):
ssh-keygen -t ed25519 -C "your_email@example.com"
2. Copy the public key to your clipboard:
cat ~/.ssh/id_ed25519.pub
3. Add the key to GitHub:
-
- Go to GitHub → Settings → SSH and GPG keys → New SSH Key
- Paste your public key and save
4. Test the connection:
ssh -T git@github.com
If successful, you’ll see:
Hi username! You've successfully authenticated.
Conclusion
SSH authentication is not just limited to Git; it is widely used in remote server access (SSH login), cloud computing (AWS, Google Cloud), CI/CD pipelines, and secure file transfers (SCP, SFTP).
I hope I have explained well how SSH keys work by using Git as an example.



